Howto: Send an email to an (OpenBSD) mailinglist...
OpenBSD version: doesn't really matter
Arch: Any
NSFP: Uhm... well
So, today i solved the little problem of me being semi-unable to send emails to OpenBSD mailing lists. Well, sending was fine, but the mails traveling onwards was not.
Specifically, i quite recently sent my first email to
misc@openbsd.org. Engagement was relatively limited, but given the rather
limited addition to the discussion, it was also not overly surprising. However,
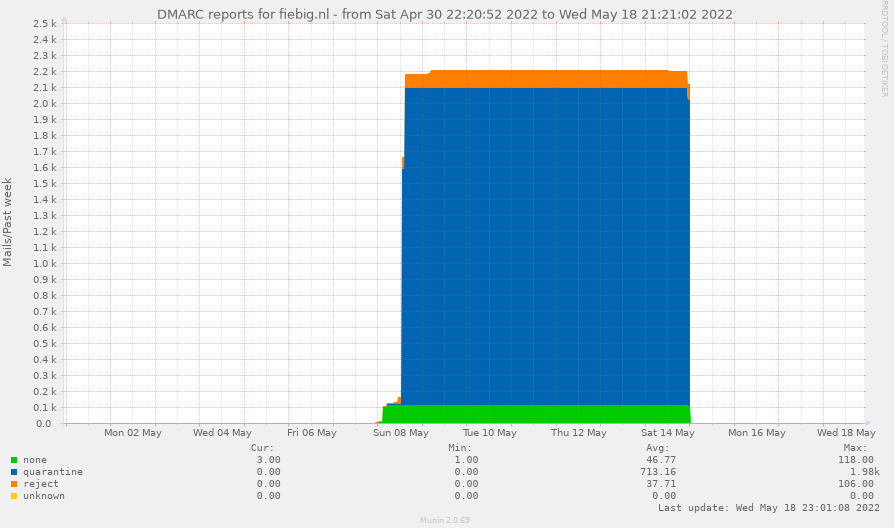
when inspecting my DMARC reports a bit later, i saw that there were uhm…
quiet unusually many emails with a from of my domain being either quarrantined
(marked as spam) or outright rejected by mailservers around the globe:
DMARC (Domain-based Message Authentication, Reporting and Conformance) is
a standard that allows you to tell the world what to do with
emails with a From: from your domain if they do not align in SPF
or DKIM. DMARC also allows you how people should let you know what
they do with your emails and erm… why.
So after sending an email to misc@openbsd.org, i found myself with reports
for around 2.2k email deliveries where messages with a from of my domain were
either put into quarrantine (=spam) or outright rejected. Closer inspection
revealed that all of these mails were either sent directly from the OpenBSD
list servers, or in some form of setting that looks like additional mail
forwarding.
Why things break
So, what happened here? For that, we first have to take a look at my DMARC and SPF policies:
SPF:
fiebig.nl. IN TXT "v=spf1 ip4:195.191.197.3 ip6:2a06:d1c0:dead:1::3 -all"
What this policy essentially says is ‘there is one IPv4 and one IPv6 address that are allowed to send emails for this domain. Everyone else is not allowed to send emails.
In addition, my DMARC policy clarifies:
_dmarc.fiebig.nl IN TXT "v=DMARC1; p=reject; rua=mailto:dmarc@aperture-labs.org"
If a policy (SPF or DKIM) is not fulfilled, reject that email; Please report handling of mail for this domain to dmarc@aperture-labs.org (please do not spam that address, a poor perl script will have to read all of your messages).
So, what happens is that i send an email to misc@openbsd.org, and it gets
dutifully forwarded to all subscribers. However, the subscribers’ mail-servers
notice that these messages are not coming from an address that is allowed to
send, and reject the message. Technically, the OpenBSD mailers apply
SRS, the Sender Rewriting Scheme. However, DMARC hard-matches on
mail-from, not envelope from:
DMARC uses the result of SPF authentication of the MAIL FROM identity.
Technically, this would be the point where DKIM could spring to the resque. Of
course i sign all my outbound messages with DKIM, and for DMARC to pass, it
is actually sufficient to have one of the two (SPF or DKIM) align with the
from domain and validate. However, it seems like the OpenBSD mailinglist
actually strips DKIM (at least i have not found any mail in my inbox with DKIM
headers; interestingly, X-Google-DKIM-Signature: headers remain intact. Of
course there is a reason for this, specifically, that majordomo allows you to
modify subject and from headers, depending on user configuration.
Solutions without changing the ML
So, what can we do about this? Well, first of all, i want to allowlist the
OpenBSD mailservers on my mailserver. Otherwise, I am going to miss out on all
other domains that feature a DMARC policy of p=reject. Alternatively, i could
actually try to convince majordomo to rewrite From: for all list mails.
However, neither of these steps solves the issue of my mails being rejected
by others. Of course, I could just go for a more permissive DMARC policy
(p=none) or add the OpenBSD mailer to my SPF policy. However, i kind of want
to keep p=reject, and I am also a fan of a rather slim SPF set.
So, in the end, i just went for registering reads-this-mailinglist.com (Note, technically a subdomain should be fine as well… but i thought this would be kind’a fun), using it specifically for mailinglist subscriptions, and adding the following DMARC and SPF policies to it:
_dmarc.reads-this-mailinglist.com. IN TXT "v=DMARC1; p=none; rua=mailto:dmarc@aperture-labs.org"
reads-this-mailinglist.com. IN TXT "v=spf1 ip4:195.191.197.3 ip6:2a06:d1c0:dead:1::3 ?all"
And now… i should be able to post again… with people actually receiving my mails.
Solutions where the list has to change
Another option that might be able to solve this problem (without changing DMARC policies) would be using ARC (Authenticated Receive Chains) on the list servers. However, as simple–essentially DKIM with extra steps for forwarders–this may sound, it also comes with a large set of caveats, and despite the nice idea, the set of mail servers trusting other mail servers’ ARC signatures is ‘not that big’. So, while in theory, this might be a solution, the practice of the Internet makes it ‘not really a solution’. So… back to reads-this-mailinglist.com, i guess…
Closing remarks
Et ceterum censeo, electronic nuntius est pulmentum.